Thousands of iOS and Android mobile applications are exposing more than 113 GB of data through more than 2,271 misconfigured Firebase databases, according to a report released this week by mobile security company Appthority.
Firebase is a Backend-as-a-Service offering from Google that contains a vast collection of services that mobile developers can use to build mobile and web-based applications.
The service is incredibly popular with leading Android developers, providing cloud messaging, push notifications, databases, analytics, advertising, and a host of other backends and APIs that can easily connect to your projects and benefit from large-scale services.
Appthority scanned over 2.7 million mobile applications
Beginning in January 2018, Appthority researchers scanned mobile applications that used Firebase systems to store user data and analyzed the application’s communications pattern for requests made to Firebase domains.
Researchers searched in particular for applications that connected to Firebase-based JSON URLs that, when accessed directly, allowed any unauthorized third party to view all application data.
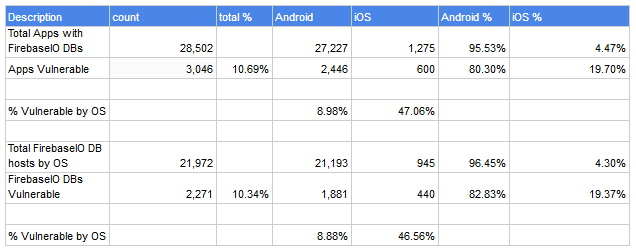
After scanning more than 2.7 million iOS and Android applications, researchers said they identified 28,502 mobile applications (27,227 Android and 1,275 iOS) that connected and stored data within Firebase backends.
Of these, 3,046 applications (2,446 Android and 600 iOS) saved data into 2,271 misconfigured Firebase databases that allowed anyone to view their content.
In total, the databases displayed more than 100 million user data records. The filtered data weighed over 113 GB and included data such as:
✏ 2.6 million plaintext passwords and user IDs
✏ 4 million PHI (protected health information) records (chat messages and prescription details)
✏ 25 million GPS location records
✏ 50 thousand financial records including bank, payment and Bitcoin transactions
✏ 4.5 million Facebook, LinkedIn, Firebase and user tokens records
Appthority says Android versions of leaky apps have only been downloaded more than 620 million times from the official Google Play store, suggesting that some popular apps were running with security issues in these backends.
Google notified to exposed applications and servers
The security company also said it notified Google of this issue before publishing its report and provided a list of affected applications and Firebase database servers.
This is not the first time Appthority has discovered that the application’s back-end servers are exposing critical user data. Last year, the company released the HospitalGown report revealing that more than 1,000 applications were exposed through 43 TB of user data through the MongoDB, Redis, CouchDB, Elasticsearch, and MySQL backend servers.
Also last year, Appthority researchers discovered that dozens of developers had left the API credentials in hundreds of applications built around the Twilio service, exposing customer private call recordings and SMS text messages.